Governance & Compliance
Our goal is to ensure your IT investments generate business value and mitigate risk.
What is Governance & Compliance?
Governance and Compliance involves maintaining the standards defined by legal mandates, contractual obligations, and internal polices and standards. Once you develop an information security strategy that aligns to your business objectives, these policies and activities take you to the next level.
Failure to comply with government regulations can lead to adverse legal implications and potential financial penalties. SCS brings a deep understanding of data privacy regulations and best practice security frameworks. We can help you develop a strategy and implement the technical and administrative controls to achieve compliance with any of these regulations.
Our Security Framework
- Risk assessment and planning
- Tracking of metrics
- Investigation of anomalies
- CMMC Compliance Assessment
- SSP and POAM development and management
- Mitigation of well-known operational or security violations
- Monitoring and responding to industry regulatory trends
- Integration of assurance initiatives across the organization
- Mapping operational activities to recognized frameworks and standards
- Compliance indicates to your customers that you have made arrangements to ensure your sustained operations, even in the face of adversity; that you have pursued a “Strategy of Readiness and Resilience.”
Examples of Compliance Activities Include
Common Compliance Standards
Federal Information Security Management Act of 2002

Protection of the nation’s security interests is governed by FISMA, the Federal Information Security Management Act. To protect the government’s security position, and those of its contractors and partners, the National Institute of Standards and Technology (NIST) has developed a wide range of controls requirements and guidance manuals, which defines the detailed specifications for security, privacy and risk management controls.
If your organization plans to conduct business with the US Federal Government, then these security controls must be implemented, continuously monitored and periodically tested to ensure that your information system is trustworthy enough to process federal information. IF you comply, your reward is an Authority to Operate (ATO), which is granted by the federal agency’s office of Information Security. The ATO is a precursor to conducting business with the US Government.
Agencies must adhere to the framework’s 200+ controls that are defined in NIST Special Publication 800-53,
Security and Privacy Controls for Federal Information Systems and Organizations.
The prescriptive controls are organized by the following control families:
- Access Control
- Security Awareness and Training
- Audit and Accountability
- Security Assessment and Authorization
- Configuration Management
- Contingency Planning
- Identification and Authentication
- Incident Response
- System Maintenance
- Media Protection
- Physical and Environmental Protection
- Security Planning
- Risk Assessment
- Systems and Services Acquisition
- System and Communication Protection
- System and Information Integrity
- Information Security Program Management
- Data Privacy
While implementation and ongoing compliance can be strenuous effort, SCS can help. We have managed FISMA compliance for organizations supporting a range of federal agencies.
Contact us for a complimentary, preliminary consultation.
NIST Cybersecurity Framework (CSF)
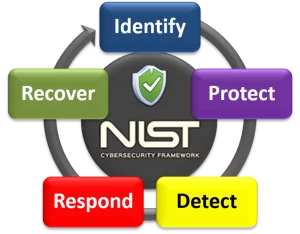
The NIST Cybersecurity Framework (CSF) was originally developed as a policy framework for Information Security for use by critical infrastructure operators. Since its introduction in 2014, the use of the NIST CSF has grown significantly across a wide range of organizations, because of its flexibility to meet organizational differences, its focus on risk-based management of outcomes, and its guidance for setting goals and measurement of security maturity against those goals.
The CSF leverages the controls defined in NIST Special Publication 800-53, Security and Privacy Controls for. Federal Information Systems and Organizations, and NIST Special Publication 800-171 controls, Protecting Controlled Unclassified Information (CUI) in Nonfederal Systems. NIST SP 800-53 is suitable for Federal Agencies and Contractors, while NIST SP 800-171 is a slimmed down version of the controls, suitable for most commercial organizations, state and municipal government agencies.
We like to use the NIST CSF as a basis for cybersecurity strategy, because it enables clear management oversight of current security posture, future maturity goals and progress on the path to meet stated goals.
Contact us for an introductory assessment of your organization. We can provide more information about how to utilize the CSF for your cybersecurity strategy.
The Health Insurance Portability and Accountability Act of 1996

HIPAA ( Pub.L. 104–191, 110 Stat.1936) was enacted in 1996 to improve portability and continuity of health insurance coverage for workers and their families when they change or lose their jobs. HIPAA requires the establishment of national standards for electronic health care transactions and national identifiers for providers, health insurance plans and employers.
HIPAA includes numerous sections and requirements. However, two key rules pertain to information security requirements:
- The Privacy Rule mandates how covered entities protect, share and manage Protected Health Information (PHI).
- The Security Rule defines the administrative, physical and technical safeguards for Electronic PHI.
Covered entities must apply security and data privacy controls to the ensure the protection of PHI, including formal governing policies and procedures, technical safeguards and training of all users who may access this data.
Covered entities may include:
- Health care providers that conduct transactions in electronic form;
- Health plans; and
- Health care clearinghouses.
If you need to strengthen your security or develop a Data Privacy program to comply with HIPAA, contact us today to schedule an initial, no cost consultation.
The Payment Card Industry Data Security Standard (PCI DSS)

PCI DSS is a comprehensive standards framework defined by the Payment Card Industry Security Standards Council to protect the security pf payment card data security. PCI DSS activities include formal definition of prevention, detection and incident response protocols and controls.
Merchants who process payment cards must self assess and attest that their information security environment conforms to the requirements of the standard. Merchants are subject to quarterly external technical scans by a Qualified Security Assessor (QSA), as well as an annual validation of adherence to the standard.
At a high level, the major requirements of PCI DSS include:
- Install and maintain a firewall configuration to protect cardholder data.
- Do not use vendor-supplied defaults for system passwords and other security parameters.
- Protect stored cardholder data.
- Encrypt transmission of cardholder data across open, public networks.
- Use and regularly update antivirus software.
- Develop and maintain secure systems and applications.
- Restrict access to cardholder data by business need-to-know.
- Assign a unique ID to each person with computer access.
- Restrict physical access to cardholder data.
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
- Maintain a policy that addresses information security.
Any organization that processes, stores or transmits credit card information is expected to conform to the standard.
Contact us today for a no obligation conversation about your PCI DSS compliance needs. We can help.
The Sarbanes-Oxley Act of 2002 / COBIT 5
SOX was enacted by the federal government in response to the malfeasance of companies like Enron and Worldcom. While most of the regulation concerns accounting rules, Section 404 contains the rules for Information Security.
Where accounting adheres to the much broader COSO (Committee of Sponsoring Organizations of the Treadway Commission) framework, Information Security is addressed in the COBIT 5 framework. COBIT (Control Objectives for Information and Related Technology) provides instruction to design and implement your enterprise security strategy that supports your business mission and culture.
COBIT provides the following required benefits:
- Framework for risk mitigation
- Strategic control objectives for optimal IT governance and enabling control practices
- Generic IT, Information Security and Assurance management processes
- A popular framework for security compliance with SOX
Contact us today to discuss your SOX compliance issues, and to find out how we can help.
EU General Data Protection Regulation

The EU General Data Protection Regulation (GDPR) was enacted to protect the privacy rights of EU Residents.
The EU General Data Protection Regulation was enacted to protect the privacy rights of EU Residents. GDPR represents a significant risk to US organizations who market products or services to European Union residents, or who have prior existing relationships with EU customers. In fact, if your organization processes data on behalf of a client that has European customers, you must comply with GDPR.
- Effective May 25, 2018
- Extends privacy protections and rights of EU residents beyond EU boundaries
- Issues noncompliance penalties, which can total 4% of annual revenue or €20 Million (whichever is greater)
- Replaces the EU Data Protection Directive
There are major differences between GDPR and any previous regulation impacting American business.
- The definition of personal data is significantly broader than American PII or ePHI. Personal data includes email addresses, web browsing or shopping history (cookies) and location identifiers.
- GDPR defines strict rules for the processing and storing of EU citizens’ personal data
- Personal data must be tokenized (pseudonymization). Individual identifiers (personal data components) must be stored separately. The process of pseudonymization differs from US Anonymization methods prescribed by HIPAA and GLBA.
- If your organization suffers a data breach, in which personal data was accessed, you must report the Incident to EU Authorities and the affected Data Subjects within 72 hours of detection.
- You should revise your Incident Response Plans to account for this disclosure schedule.
- Broader individual protections than U.S. Privacy Laws.
- Data Subjects must provide explicit consent (Opt In) before your organization can process their data. In the US, most collected consent is implicit, and organizations offer the right to Opt Out.
- Data Subjects can also opt out at any time, and can demand to be forgotten. Can your systems forget a Data Subject on demand?
- Your organization must provide Privacy Statements and mechanisms for Data Subjects to grant consent, in clear language and without repercussion.
Do you need help with a strategy to comply with GDPR? SCS can help.
ISO 27001

ISO 27001 is an information security standard published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). ISO 27001 specifies an Information Security Management System (ISMS), which comprises a comprehensive set of management controls, designed to provide oversight and conform to an acceptable standard of practice.
ISO/IEC 27001 requires that management:
- Systematically examine the organization’s information security risks, taking account of the threats, vulnerabilities, and impacts;
- Design and implement a coherent and comprehensive suite of information security controls and/or other forms of risk treatment (such as risk avoidance or risk transfer) to address those risks that are deemed unacceptable; and
- Adopt an overarching management process to ensure that the information security controls continue to meet the organization’s information security needs on an ongoing basis.
A sister standard, ISO 27002 specifies a set of specific information security controls, most of which should be implemented by the organization. However, the organization may tailor the set to meet its needs, in accordance with its risk profile.
While many organizations may utilize ISO 27002 controls independently from each other, ISO 27001 specifies the system in which the controls work together to solidify a security infrastructure suitable to protect against most cyber threats. Organizations that meet the requirements may be certified by an accredited certification body following successful completion of an audit.
SCS offers strategic and operational guidance and implementation of an ISMS in accordance with the ISO 27001 standard. We will guide you through the preparation process, and ensure you are ready for the independent certification audit. We will serve as your trusted advisor throughout the process, and can even facilitate the Certification Audit on your behalf.
If you are interested in pursuing ISO 27001 compliance, contact us today for an introductory assessment to determine the scope of your project.
